The new generation of cybersecurity defenses must protect against never-seen-before attacks even before they are devised by the attackers. In early December 2023, a security researcher at SafeBreach presented a paper (Alon Leviev Security Researcher, SafeBreach – December 6, 2023 Blackhat UK) at BlackHat Europe describing new process injection techniques utilizing Windows thread pools to attack a system. The researcher wanted to see if:
- A legitimate feature of the OS could be abused to execute a process injection.
- The current best of breed EDR solutions could detect a legitimate versus a malicious use of a feature.
- The current detection approach is generic enough to find a variety of versions of the attack.
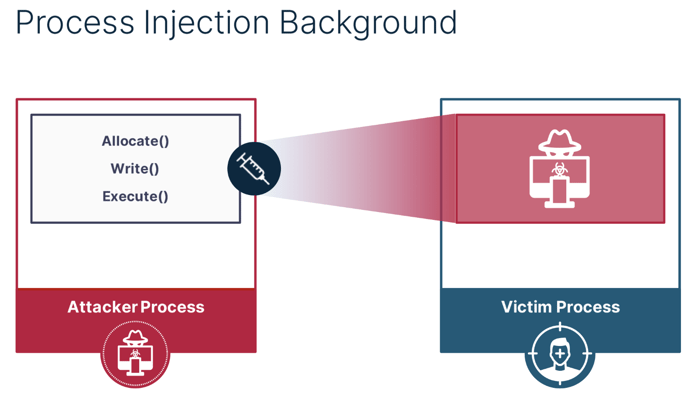
They identified eight new process injection techniques taking advantage of Windows thread pools. More importantly, these techniques were found to be fully undetectable when tested by the researcher against five of the leading cloud based NGAV/EDR solutions. These solutions were unable to effectively distinguish between legitimate and malicious uses of an OS feature.
The test harness named “PoolParty”, because it uses the thread pools in the Windows OS as an attack vector for process injection, can be easily downloaded and run on a system under test. The intrusion techniques can trigger malicious execution as a result of a legitimate action.
The researchers concluded that current detection approaches are unable to generically detect new process injection techniques, opening the door for sophisticated threat actors to explore innovative new methods for process injection. Their two major takeaways were:
“Although EDRs have evolved, the current detection approach utilized by most solutions is unable to generically detect new process injection techniques like those we have developed here. While our research demonstrates how we were able to abuse thread pools specifically, malicious actors will undoubtedly find other features to leverage in a similar way. We believe it is critical for EDR vendors to develop and implement a generic detection approach to proactively defend against these possibilities.”
“We also believe it is important for individual organizations to enhance their focus on detecting anomalies, rather than placing complete trust in processes based solely on their identity. Our research demonstrates that executing code on the behalf of a trusted process can go undetected by an EDR. This underscores the importance of deeper inspection to ensure the legitimacy of operations performed by such processes.”
This information was shared with EDR and OS vendors with the goal of hardening the attack surface and improving detection capabilities.
Interestingly as soon as Red Team members at ARIA learned of the paper, they downloaded the test harness and ran it against a test system protected by ARIA AZT (ARIA ZERO TRUST) PROTECT. Out of the box, with no enhancements, no cloud updates, no special configuration necessary, ARIA AZT detected and automatically blocked each attack variation’s injections from executing. To find out more – ask for a demo.
ARIA AZT PROTECT uses a patented approach to lock down critical applications from exploitation, while blocking the execution of zero-day malware, and automatically stops the sophisticated techniques used by the most advanced nation-state sponsored attackers. It also deploys in minutes and instantly provides full protection, requiring no configuration to stop these attacks. It works in true air-gapped infrastructures and deploys on legacy, out-of-support OS-based critical devices, in addition to today’s latest systems. Its ability to utilize less than 2% of a single CPU core and less than 100 MB of device memory ensures it never disrupts or adds latency to the critical applications it protects. Furthermore, it deploys without requiring any reboots of the protected device OS or the hosted applications.
If you need support building-out a simple to implement active defense, please contact CSPi Technology Solutions.
The blog post was originally posted on the Aria Cybersecurity Solutions website.